Other provider
Control access to BugSnag using a SAML SSO provider.
BugSnag’s Single Sign-On solution provides:
- Authentication and authorization (SAML)
- User provisioning and deprovisioning (SCIM)
For specific documentation for Okta, OneLogin and other supported providers, please see the supported providers.
Setup SAML
To configure SAML (Organization admin access required):
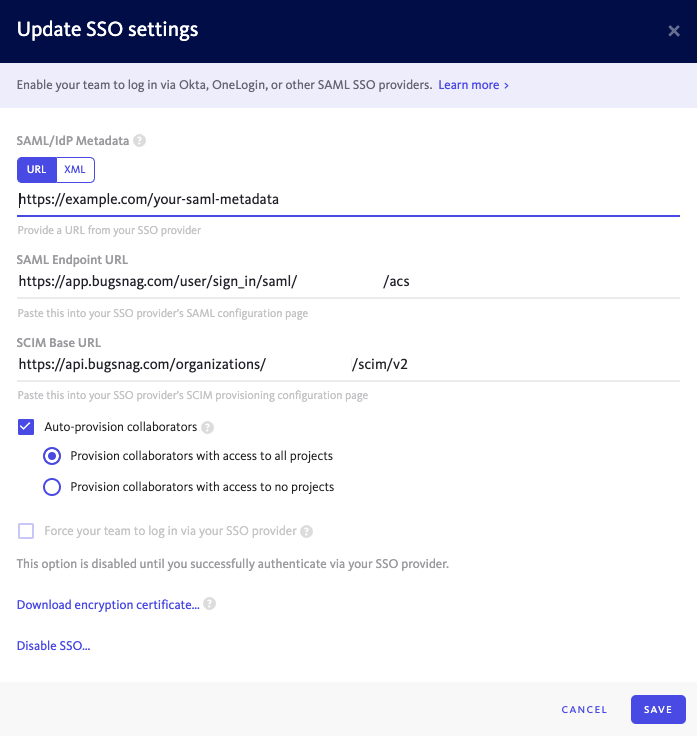
In your BugSnag dashboard, select Single sign-on from your organization settings (shortcut:
go):- Copy the SAML endpoint URL to your clipboard.
- Download the encryption certificate (optional, if you want to configure your SSO provider to encrypt SAML assertions).
In the SSO provider create a SAML app:
- Configure the Service Provider (SP) Entity ID (used to validate the audience) with
https://app.bugsnag.com.
(Note – use this ID for all dashboards, even for organizations on the BugSnag for Enterprise instance or On-premise unless theSSO_ENTITY_IDenvironment variable has been set.) - Paste the URL copied from your BugSnag dashboard into the provider’s configuration. This may be called Assertion Consumer Service (ACS) URL or something similar.
- Ensure you are providing an email address as the name identifier in the SAML assertion. You can check that the
NameIDFormatelement in your SAML metadata is set toemailAddressto verify this. - (Optional) Configure attributes called
User.FirstNameandUser.LastName. If not supplied each user’s email address will be used as their name. - (Optional) Upload the encryption certificate from your BugSnag dashboard if you want to encrypt SAML assertions.
- Find a URL to the provider metadata and copy to your clipboard (the URL not the metadata itself).
- Configure the Service Provider (SP) Entity ID (used to validate the audience) with
In your BugSnag dashboard:
- Paste the Metadata URL (recommended) or XML Metadata in the SAML/IdP Metadata field.
- Select Auto-provision collaborators if you would like accounts to be automatically created for new users when they first log in (see SCIM for full provisioning and deprovisioning support).
- Select whether users will be granted access to all current projects or no projects by default. Users will only be added up to your plan’s collaborator limit. After provisioning, access to projects can be managed by any Admin.
- Select Enable SSO.
You can now log in to your BugSnag dashboard from your SSO provider.
Setup provisioning and deprovisioning (SCIM)
Provisioning and deprovisioning is available on Enterprise plans.
The following provisioning and deprovisioning features are supported:
- Create users
- Update user names and email addresses
- Deactivate users
In your BugSnag dashboard, select Personal auth tokens from the user settings (shortcut:
gu) of an organization administrator:- Generate a new auth token which will be used for SCIM.
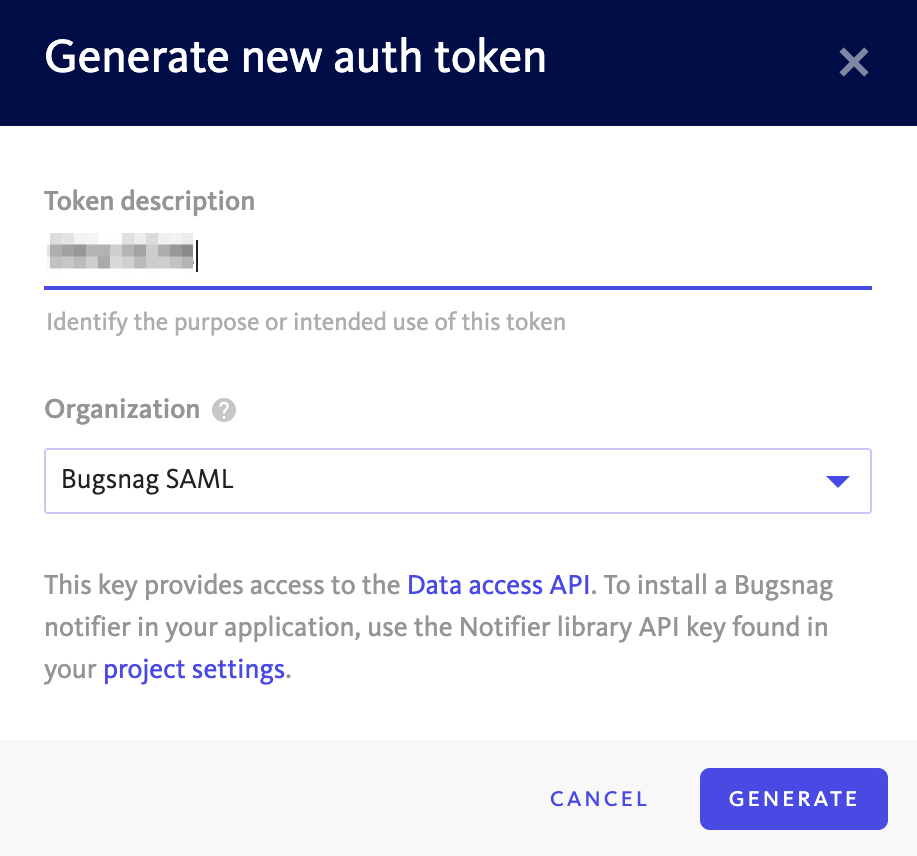
- Generate a new auth token which will be used for SCIM.
Select Single sign-on from your organization settings (shortcut:
go):- Copy the SCIM Base URL.

- Copy the SCIM Base URL.
In the SSO provider create a SAML app:
- Enable provisioning and enter the SCIM Base URL and auth token.
- Email address is used as the SCIM username.
Users can now be automatically provisioned and deprovisioned from your SSO provider.
Session Timeout
If a SessionNotOnOrAfter value is present in the SAML authentication response, it will be used to set the timeout of the BugSnag session.
Please refer to your SSO provider’s documentation for more information on how to configure SessionNotOnOrAfter.