Okta setup
Control access to BugSnag using Okta.
The Okta integration provides:
- Authentication and authorization (SAML)
- User and group/team provisioning and deprovisioning (SCIM)
Setup SAML
To configure SAML (Organization admin access required):
In your BugSnag dashboard, select Single sign-on from your organization settings (shortcut:
go):- Copy the SAML endpoint URL to your clipboard.
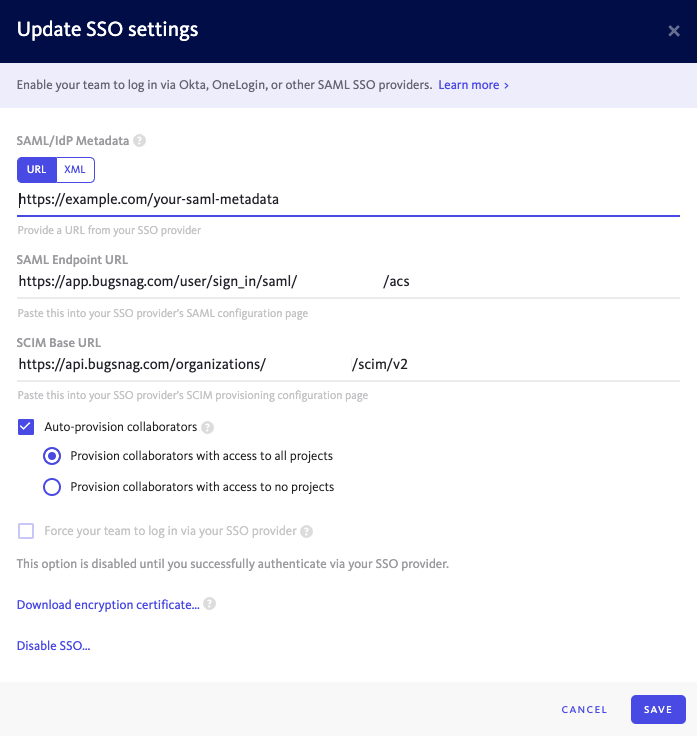
- Copy the SAML endpoint URL to your clipboard.
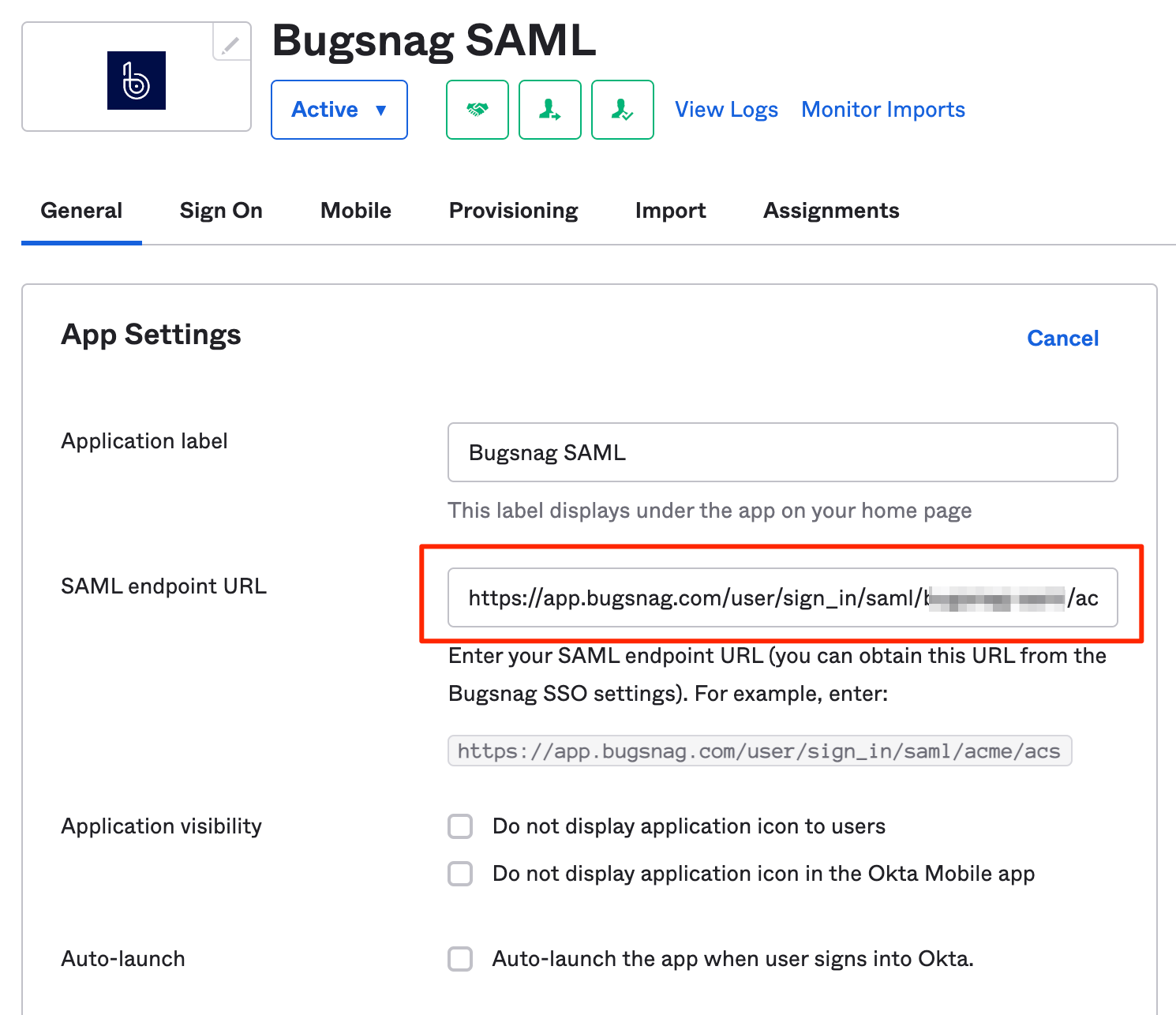
In Okta Admin, select Applications then Browse App Catalog and search for “Bugsnag SAML”. Select Add Integration.
In General Settings:
- SAML Endpoint URL – Paste the URL copied from your BugSnag dashboard.
- Select Next, assign users as required, then Done.
In the Sign On tab:
- Under SAML Signing Certificates, select Actions and copy the link to the IdP metadata to your clipboard (the URL not the metadata itself)
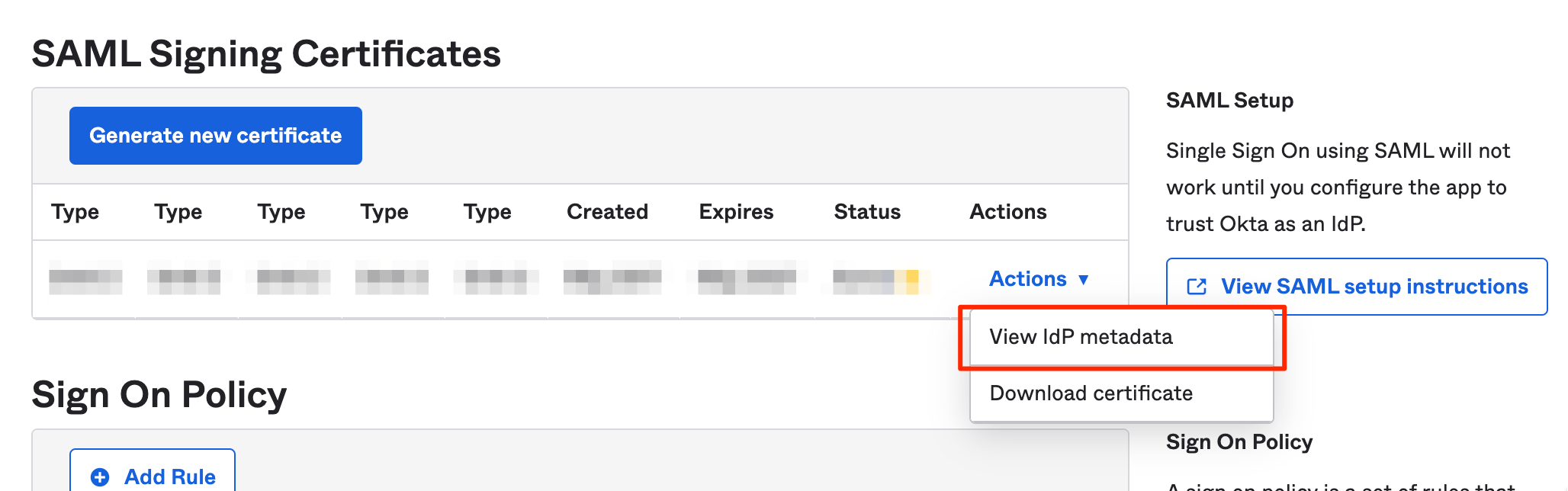
- Select Next.
- Under SAML Signing Certificates, select Actions and copy the link to the IdP metadata to your clipboard (the URL not the metadata itself)
In your BugSnag dashboard:
- Paste the IdP metadata URL in the SAML/IdP Metadata field.
- Select Auto-provision collaborators if you would like accounts to be automatically created for new users when they first log in (see SCIM for full provisioning and deprovisioning support).
- Select whether users will be granted access to all current projects or no projects by default. Users will only be added up to your plan’s collaborator limit. After provisioning, access to projects can be managed by any Admin.
- Select Enable SSO.
Users assigned to the app in Okta can now log in to your BugSnag dashboard.
Setup provisioning and deprovisioning (SCIM)
Provisioning and deprovisioning is available on Enterprise plans.
The following provisioning and deprovisioning features are supported:
- Create users
- Update user names and email addresses
- Deactivate users
- Push groups
To configure access (Organization admin access required):
In your BugSnag dashboard, select Personal auth tokens from the user settings (shortcut:
gu) of an organization administrator:- Generate a new auth token which will be used for SCIM.
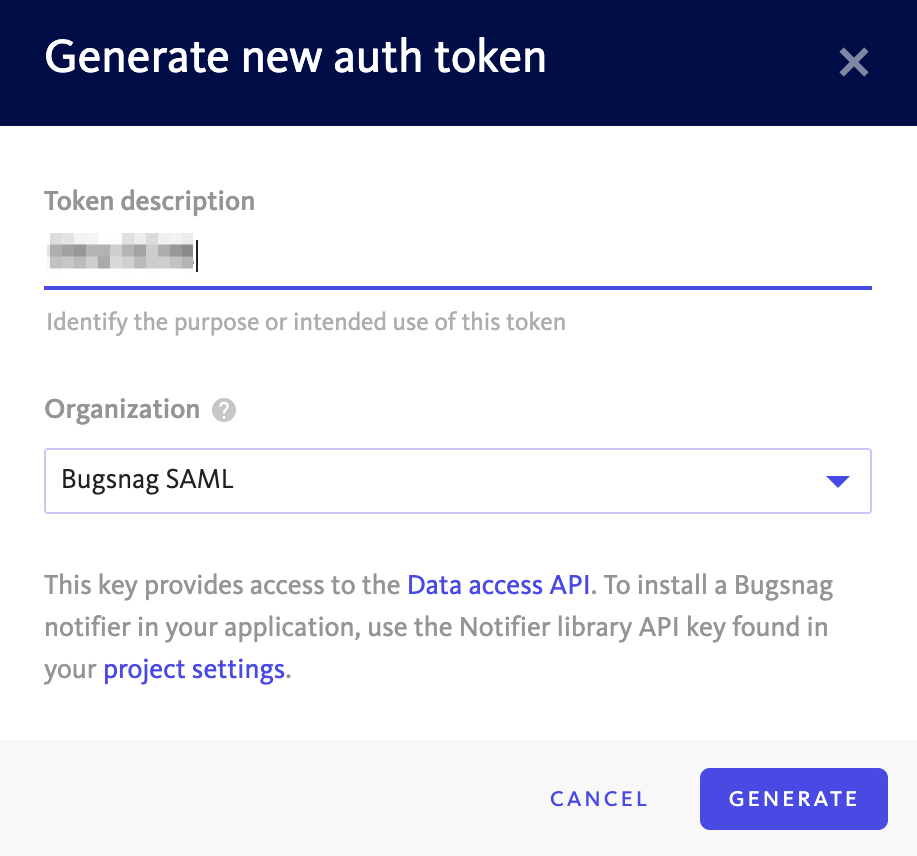
- Generate a new auth token which will be used for SCIM.
Select Single sign-on from your organization settings (shortcut:
go):- Copy the SCIM Base URL.

- Copy the SCIM Base URL.
In Okta Admin, open the configuration for the “Bugsnag SAML” application and in the Provisioning tab.
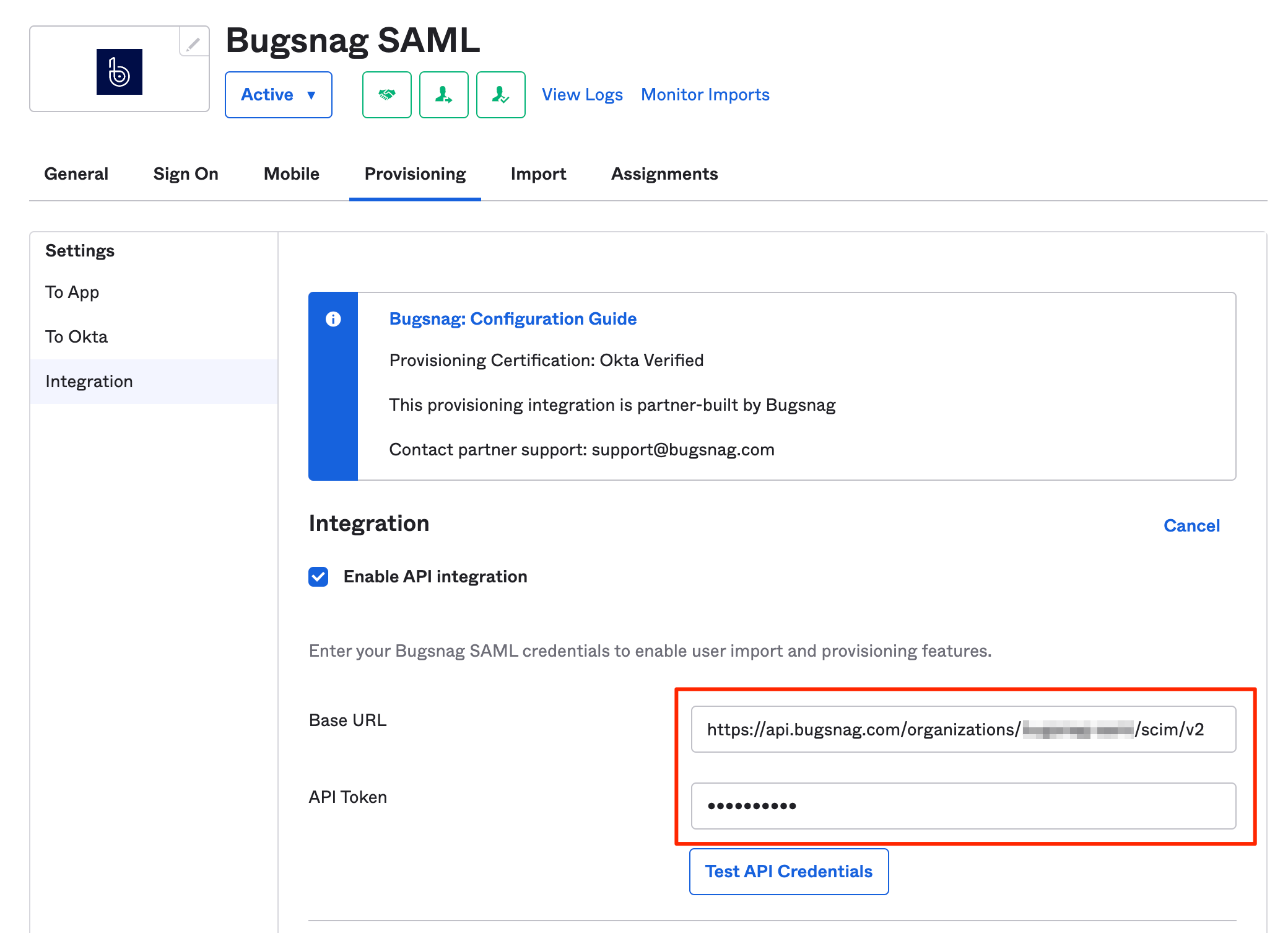
- Enter the SCIM base URL and auth token in the Integration section.
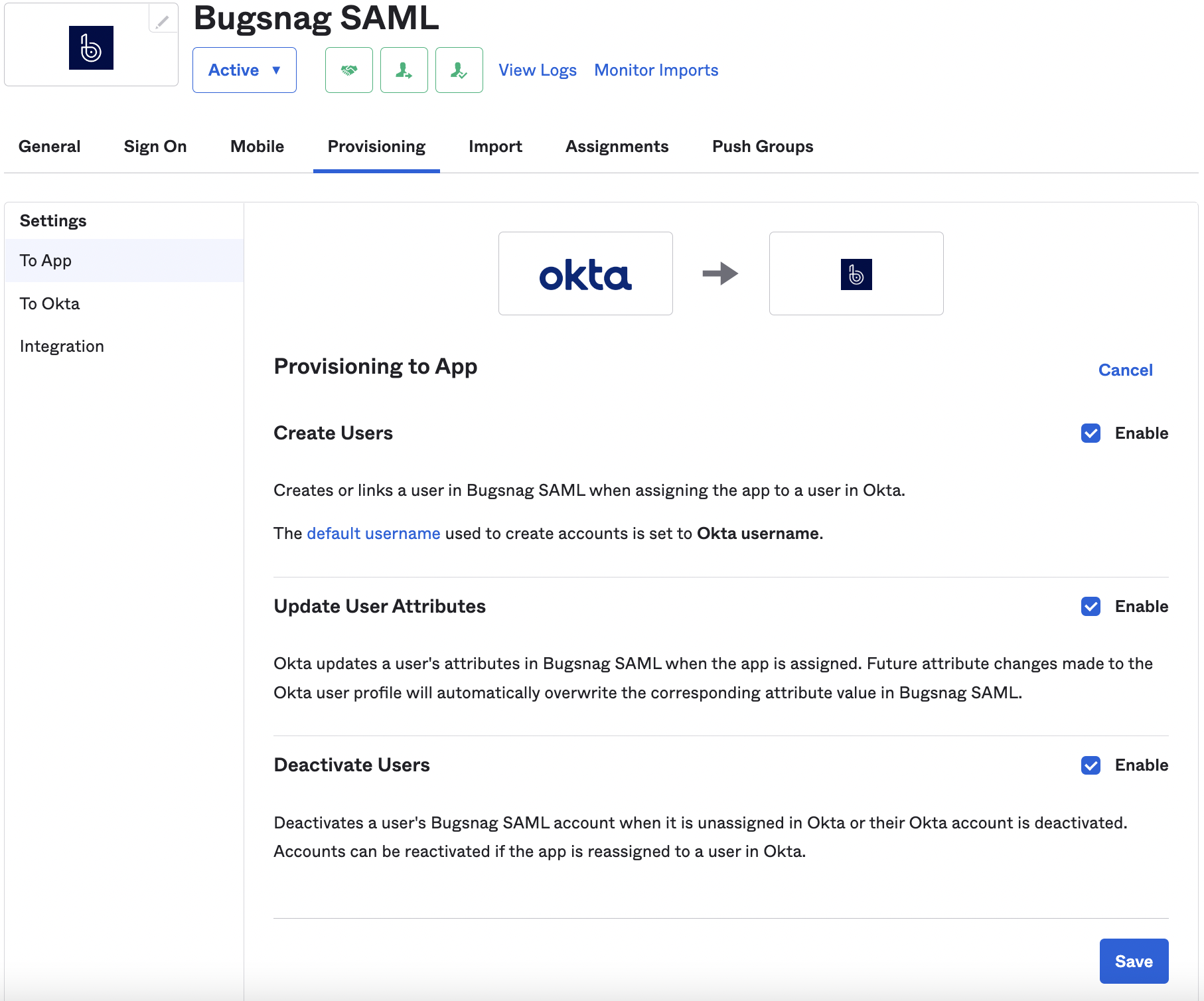
- Ensure the provisioning options are enabled in the To App section.
- Enter the SCIM base URL and auth token in the Integration section.
In the Sign On tab:
- Ensure Application username format is set to Email.
Session Timeout
If a SessionNotOnOrAfter value is present in the SAML authentication response, it will be used to set the timeout of the BugSnag session.
Please see the Okta documentation for information about setting SessionNotOnOrAfter in your SAML responses.
Known issues
None.